Report: Id Has Turn into a Essential Safety Perimeter for Cloud Companies
A brand new risk panorama report factors to new cloud vulnerabilities. Based on the 2025 Global Threat Landscape Report from Fortinet, whereas misconfigured cloud storage buckets have been as soon as a first-rate vector for cybersecurity exploits, different cloud missteps are gaining focus.
“Cloud providers now sit on the heart of recent operations, and id has turn out to be one of the crucial crucial safety perimeters,” stated a post exploring the report from the corporate’s FortiGuard Labs. “Cloud breaches are not restricted to misconfigured storage buckets. As infrastructure migrates to the cloud, attackers are discovering acquainted footholds to use, equivalent to over-permissioned identities, credential leaks in public code repositories, and lateral motion via cloud-native providers.
“FortiCNAPP telemetry reveals that attackers usually start by logging in from unfamiliar geographies, generally inside hours of a developer’s official exercise. From there, they escalate privileges, set up persistence, and use official providers to mix into regular community visitors. In 2024, 25% of all cloud incidents started with reconnaissance, equivalent to API enumeration, permission probing, and discovery of uncovered belongings.”
That telemetry is essential to the report, which is predicated on Fortinet’s world sensor community and risk intelligence, and that intelligence suggests the benefit loved by risk actors is rising, and can proceed to take action till organizations change how they measure and handle threat.
One of many report’s key findings, “Cloud assaults are evolving, however misconfigurations nonetheless reign,” discusses the above discovering in larger element.
“Cloud environments stay a prime goal, with adversaries exploiting persistent weaknesses, equivalent to open storage buckets, over-permissioned identities, and misconfigured providers,” the report stated. “Lacework FortiCNAPP telemetry reveals a gradual rise in cloud compromises, usually involving id abuse, insecure APIs, and privilege escalation. These vectors are continuously mixed in multi-stage assaults that leverage automation and bonafide providers for stealth and persistence. Reconnaissance stays essentially the most prevalent tactic, with attackers probing APIs, enumerating permissions, and scanning for uncovered belongings. In 70% of noticed incidents, attackers gained entry via logins from unfamiliar geographies, highlighting the crucial position of id monitoring in cloud protection.”
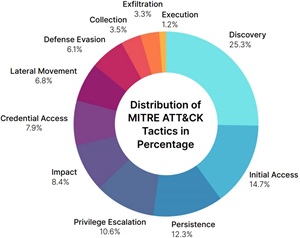
The MITRE ATT&CK tactic distribution chart above reveals some key takeaways of its personal:
- Discovery (25.3%): The most typical tactic in cloud assaults, indicating widespread scanning, enumeration of permissions, and probing of APIs and providers.
- Preliminary Entry (14.7%): Attackers most frequently achieve entry via leaked or stolen credentials, phishing, or misconfigured authentication settings.
- Persistence (12.3%): Adversaries create or modify cloud identities and roles to take care of long-term entry to compromised environments.
- Privilege Escalation (10.6%): Attackers manipulate permission insurance policies or exploit cloud APIs to raise their entry rights.
- Affect (8.4%): Actions geared toward disrupting providers, tampering with knowledge, or initiating ransomware-like assaults within the cloud.
- Credential Entry (7.9%): Strategies used to extract keys, passwords, or tokens for lateral motion or additional exploitation.
- Lateral Motion (6.8%): Motion between cloud providers, areas, or accounts after preliminary compromise, usually undetected.
- Protection Evasion (6.1%): Strategies used to keep away from detection, equivalent to utilizing official providers or hiding malicious habits in regular workflows.
- Assortment (3.5%): Gathering delicate knowledge or metadata for later use or exfiltration.
- Exfiltration (3.3%): Stealing knowledge from cloud storage, databases, or containers, usually via abused APIs.
- Execution (1.2%): Working malicious scripts or binaries, usually via Bash, PowerShell, or Python in cloud workloads.